If you also blindly trust the end-to-end encryption messaging apps, you’ll have to reconsider your decision after reading this. Media file jacking is sneaking into the nooks and crevices of your devices to steal your data.
Malware could change bank account number on invoice sent over #WhatsApp, #Telegramhttps://t.co/34UqCkSocl
— Express Technology (@ExpressTechie) July 16, 2019
No doubt, these tech companies ensure to stop the malicious actors from sneaking into your conversations. But, according to the security researchers at Symantec, the hackers can steal your account. And, can even scam the users by sending payments to wrong accounts.
How does “Media File Jacking” manipulate media files?
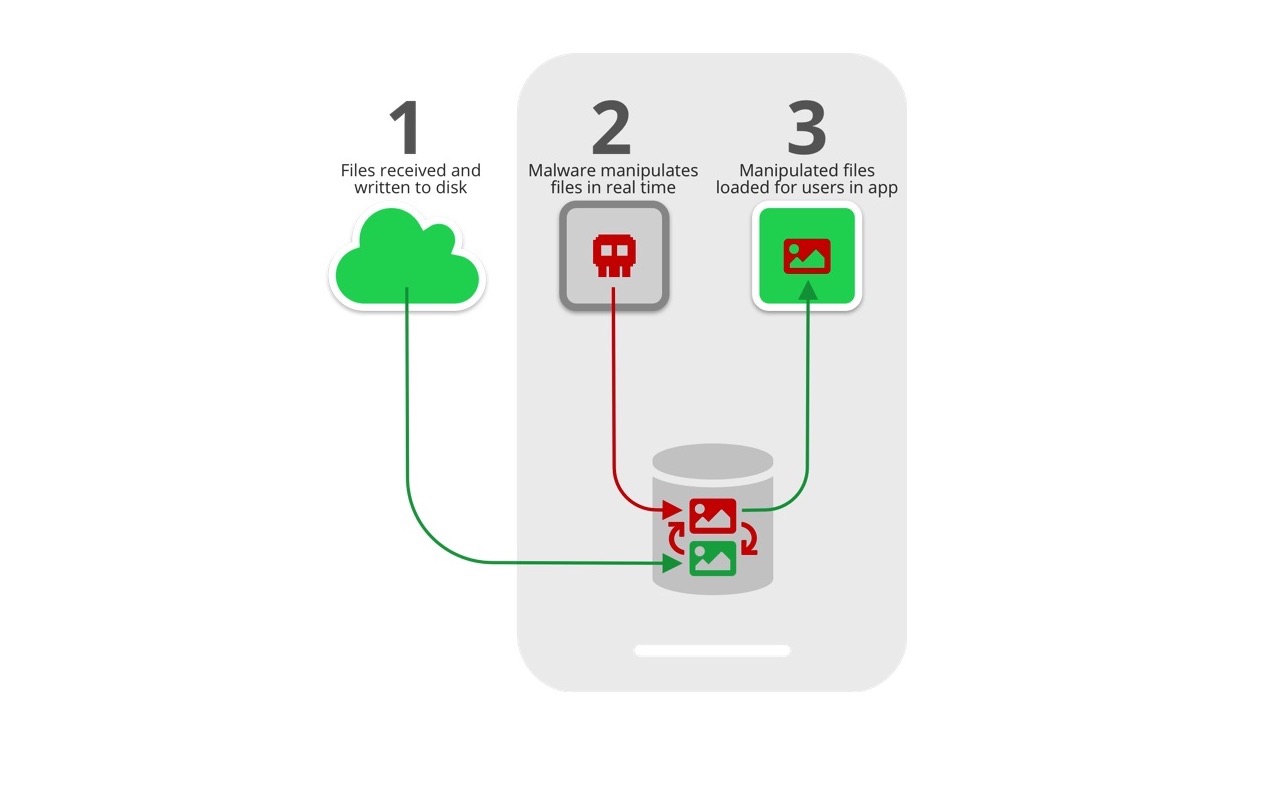
It is a known fact that the installed apps can access and rewrite the files present in the external storage of the device. This is what Media File Jacking takes advantage of.
By default, WhatsApp saves all the received media files in the external storage. On the other hand, Telegram uses internal storage for the purpose which cannot be accessed by any other app of the phone. But, many Telegram users change these settings to “Save to Gallery” to further share these media files.
One malicious app installed on the user’s device can exploit the user’s media files like private photos, videos, and documents send between the different users. And that too, without user’s knowledge.
Demonstrations by Symantec Researchers
We've uncovered an exploit affecting WhatsApp and Telegram for Android that could be used by malicious actors to modify files and trick users. Get the scoop. https://t.co/NOx1LraeSD
— Symantec by Broadcom (@symantec) July 15, 2019
The researchers demonstrate four attack scenarios using Media File Jacking. The demo shows how an innocent-seeming app present on the receiver’s phone manipulates the media files send by a user. Such a malicious app can run in the background without even user knowing about it.
1. Manipulating Images
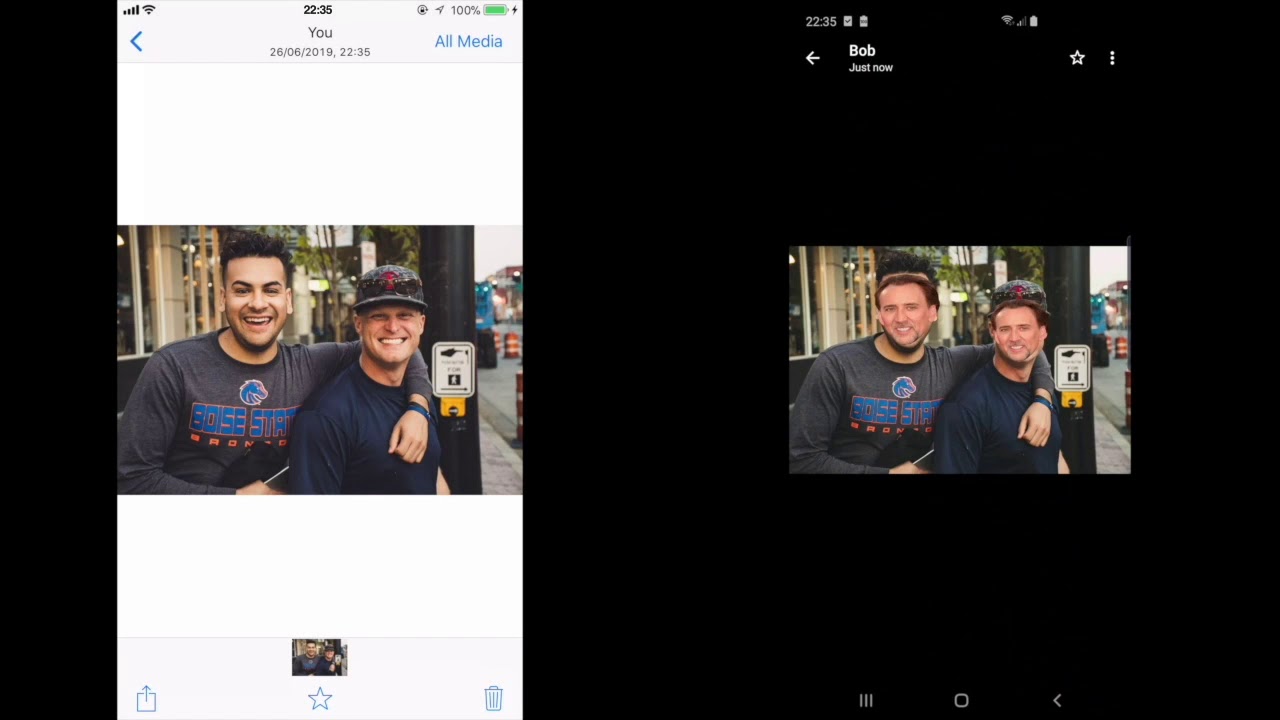
In this demonstration, the decent faces of the photo are replaced by accessing the external storage. This can be done both on receiver or sender’s end. Such manipulation can even produce some obscene pictures which might lead to extortion.
2. Manipulating Payments
Here, the malicious app present on the receiver’s device exploits the invoice shared by the sender. The invoice that appears on the receiver’s device has different account details than the one sent. This can lead the user to send payments in the wrong accounts.
3. Spoofing audio files
Here, the audio file is altered in the sender’s voice only. This can exploit the relations between the employers of an organization too.
4. Spreading fake news
The admins on Telegram use channels to share messages to an unlimited number of users at a time. The app can thus manipulate the shared media. And further, lead to the spread of fake messages among people.
How to prevent your phone from “Media File Jacking”?

The Symantec researchers have already notified Telegram and WhatsApp about this. And the Google’s new Android Q update will take this into account. This update will introduce new Scoped Storage feature. This feature will give a separate sandbox for each app. Thus it restricts other apps from using the external storage media.
By the time, you can prevent hackers from hijacking your files by taking the following steps:
- Go to WhatsApp Settings -> Chats -> Turn off “Media Visibility”
- Go to Telegram Settings -> Chat Settings -> Turn off “Save to Gallery.”
For more security updates, keep watching this space on Hiptoro.









